Proximity cards, also known as Prox cards or access control cards, are contactless ID cards or keyfobs containing programmed data.
Proximity cards, also known as Prox cards or access control cards, are contactless ID cards or keyfobs containing programmed data.
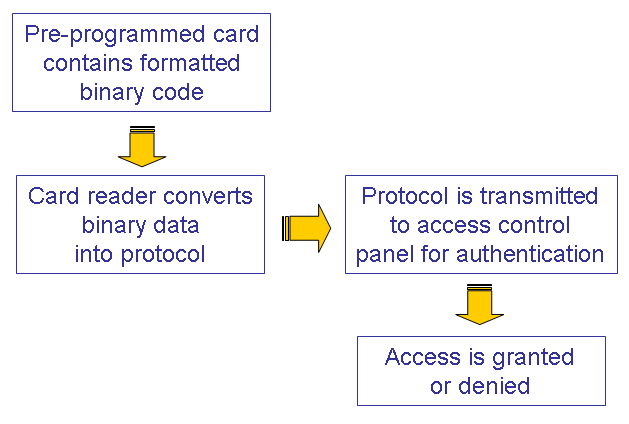
The data, or code, is “read” by a card reader and transmitted to an access control panel to control and secure physical access.
A coiled antenna and chips inside the card or keyfob hold the specific numerical programming and determine the range at which the card can be read.
HID prox cards and HID iClass contactless credentials are the gold standard in proximity technology. In this post, we outline the basics of an HID access control system and how the card is read.
Note: The following information is sourced from HID Corporation and applies to both 125 kHz Prox cards and to 13.56 MHz iCLASS® cards
Elements of a Card Access System
Any card access control system consists of four basic elements. Depending on the system’s size and purpose there may be many additional types of devices; however, the four basic elements are:
- Cards
- Readers (sometimes equipped with keypads)
- Access control panels (controllers)
- A user interface or “Host” PC
Cards
The Prox cards carry a set of binary numbers that the system uses to identify the card holder. That data is of a fixed configuration and length.
HID’s Prox cards that carry this binary type of data include:
- HID 1336 – DuoProx Card w/Magnetic Stripe

- HID 2040 – Wiegand (swipe)
- HID 1326 – 125 kHz Prox
- MIFARETM contactless smart cards
- 13.56 MHz iCLASS contactless smart cards
- 13.56 MHz iCLASS/125 kHz Prox/Magnetic stripe combination (combines three of the above technologies)
How the data is encoded on the card and transmitted to the reader varies with the technology chosen – but the card itself contains no awareness of its holder’s access privileges. Access information is held by the controller.
Readers
Standard readers convert the binary data into a protocol for transmitting to the access control panel (the controller). Each reader can only talk to its corresponding card type due to the unique technologies used in each.
Some readers can also communicate with the controller by other means, such as RS232 or Clock & Data.
Access Control Panels (Controllers)
The controller is the only part of the system where the card’s code data format can be detected and acted upon. The controller’s software works through a process of deciding whether or not to grant access. This criteria is verified in several stages:
- Length of the data format matches what the controller is expecting?
- Format structure makes sense to the controller?
- Facility Code matches?
- Site Code matches?
- Card Number is within the allotted range?
- Card Number in memory?
- Card valid at the reader at this day and time?
Controllers differ by brand and vary in how they react to incorrect card data formats. Some log a message for every “access denied” result. Others have only one generic log and others may ignore an incompatible format completely and give no reaction at all.
Therefore, in order to debug any card and card reader performance problems, it’s important to fully understand the controller’s capabilities.
User Interface or Host PC
The Host software – or user interface – is used to administer the access control system on a day-to-day basis, including:
- Adding or deleting cardholders
- Managing access privileges
- Creating and modifying schedules and lists
- Configuring system hardware
- Monitoring system events in real time
- Generating activity reports
Rarely, in some large or complex systems, the host may make access decisions, but for the majority of systems that decision is always performed by the controller.
Card Reading & Authentication Steps
Upping Security with Mutual Authentication

Both iCLASS and MIFARE are “contactless smart cards” by definition. When either are read in their normal functional mode, an additional security step takes place. The reader and the card go through a complex mathematical process where they compare security keys carried within both the card and reader. This process is called Mutual Authentication – and it ensures that the communication between the card and reader can never be copied and repeated back to the reader.
The key in the reader must match the key in the card for the authentication process to complete correctly.
Print on Adhesive Cards for Flexibility
A cost-saving generic white adhesive CR79 or CR80 overlay is used for visual identification, allowing you to reuse the original card by replacing only the printed adhesive overlay. Adhesive cards can be created and printed like any other card, using any standard card design software and ID card printer. Due to their specialized size, CR79 cards do not work in every ID card printer. Be sure to check your printer compatibility for CR79 cards. If you don’t have a compatible printer, we recommend using a CR80 Adhesive Card.
More Helpful How-to Resources
For more more helpful prox card advice, check out our popular blog posts:
- What you Need to Reorder Prox Cards
- Slot Punching Prox Cards – How to NOT Break Your Cards
- Save Big with Generic Prox Cards
- How to Program HID Proximity Cards
- HID Prox Card Programming Checklist
- How an HID Proximity (Prox) Card is Read
- Compare HID Prox Cards – 125 kHz Proximity
- Compare HID iClass Credentials – 13.56 MHz Contactless
- Compare Indala Prox Cards – 125 kHz Proximity
- Durable New HID ProxKey and iClass KeyFob Design Doubles Read Range
Questions?
For help choosing and configuring the right HID prox card to fit your needs, contact our expert sales staff at (877) 868-0012 or [email protected]. We’re happy to walk you through your card programming and appearance options.
ID Card Group offers a price match guarantee, provides free shipping on orders over $100, and accepts purchase orders.
Source: How an HID Card is “Read,” an HID Corporation Whitepaper (howHIDcardIsRead-wp-en.pdf (80.58 kb))